Top
HID’s Risk Management Solution significantly decreases fraud risk by combining multiple threat detection engines into one cohesive solution to keep digital threats at bay.
Protect Against Known and Unknown Risks
HID’s Risk Management Solution is cutting-edge and offers complete fraud prevention. Financial institutions no longer need to patch together software from various vendors in order to address digital threats and detect zero-day malware.
This AI-powered system detects, records and analyzes users' behavioral biometrics, including clicks on a website or taps on a phone, to ensure accurate identity verification, minimize vulnerabilities. All this is done seamlessly to optimize user experience.
Read our eBook "The Ultimate Guide to Risk Management Systems" to learn more >>
Get a free analysis of your organization's exposure to phishing attacks. Sign up today >>
Complete Protection From Digital Threats
Our solution encapsulates multiple forms of fraud and other threat detection methods in order to provide a single, complete security suite.
Read the latest blog post: Malware and the Threat to Mobile Banking >>
How Precise Threat Detection Works
HID’s Risk Management Solution detects threats and stops fraud using a three-engine system. The three engines constantly analyze and detect behaviors, anomalies, and threats from end-users. Every movement, every input, every slight deviation from normal contributes to a constantly updating risk score, which determines — with uncanny accuracy — if the user should be allowed in. All this is done in a way that is completely undetectable to the users ensuring a seamless user-experience.
How is HID Global's Risk Management Solution different from others in the market? View the Product Comparison Matrix here >>
Unparalleled Security With a Simple Swipe
Secure the communication channels between you and your customers.
Prevent fraud by taking your mobile first strategy to the next level, where security and usability are fully aligned with:
- A secure, 3D solution utilizing better built-in protection for eWallets, online banking and mobile payments
- Channels that can be secured using out-of-band communication protected by device-specific keys
- The assurance that the person taking the digital action is the person authorized to do so using asymmetric key cryptography
What Sets Us Apart
70% Better Detection
It’s stronger than traditional fraud detection. Stop cyber attacks like phishing and zero-day malware before they happen.
90% Fewer False Positives
Stop wasting time and money investigating non-threats, while giving users a trusted and seamless experience.
90% Reduction in Authentication Costs
Without reliance on SMS-based verification. Machine learning and AI support risk-based, adaptive authentication.
Seamless Consumer Experience
The solution is undetectable to end-users and saves them from time-consuming and unnecessary authentication steps.
Regulation Compliant
Rules-based processes make it easy to comply with data protection and central banking legislations.
Simple Deployment
A single piece of code connects your digital environments to this cloud solution. On-premise option also available.
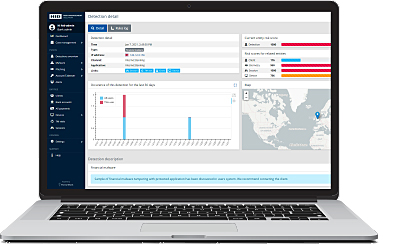
Easily Access Analytics & Adjust Business Rules
The easy-to-use dashboard provides a central viewing portal for all analytics and allows organizations to customize and use the data in novel ways. Features include:
- A rich analytical interface for viewing information — View a broad range of risk events, trends and data visualizations
- Rule-based customizations — Create custom business rules based on yes/no end-user actions
- Real-time data — Provides constant security and threat detection
- An intuitive and logical design — Simple implementation and layout make it useful for everyone