Top
Trusted access control systems safeguard your physical and digital environments. As the world leader in access control solutions, HID Global provides the highest level of security for facilities, assets, networks and resources.
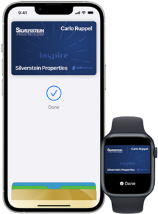
Unlock your office with iPhone and Apple Watch.
With employee badge in Apple Wallet, employees can access office doors, elevators, turnstiles, multi-function printers, and much more using just their iPhone or Apple Watch. It’s easy, convenient and secure. Employee badge in Apple Wallet integrates into existing access control systems, is simple to distribute and manage, and takes advantage of the built-in security features of iPhone and Apple Watch.
![]() Interested in using employee badge in Apple Wallet?
Interested in using employee badge in Apple Wallet?
Learn more >>
Trusted Access Control
Our award-winning access control systems extend capabilities, improve operational efficiencies and instill confidence that precious assets, resources and people are secured and protected. HID’s best-in-class access control solutions enable:
- Trusted access, for the right people at the right times
- Safe environments for employees, visitors and contractors
- User convenience and workflow optimization through integrated, mobile solutions
- Increased visibility, with real-time monitoring and cost-control functions
- Investment protection via scalable, forward-looking solutions
- Peace of mind, with expert, personalized concept-to-implementation support
With decades of experience in the development of strong access control solutions for physical and logical access, HID Global is trusted by organizations and governments to provide unsurpassed security and protection solutions.
Our Solution Portfolio
Highly Secure
HID Global develops best-in-class access control and authentication solutions that help governments and organizations stay ahead of an ever-changing threat landscape. When higher level security and privacy are paramount, our modern, integrated solutions deliver:
- Strong multi-factor authentication without disruption to user workflow and productivity.
- Complete identity and credential management over the full lifecycle of an identity—from the time trust is established to the retirement of a credential.
- PIV-enabled access control, compliant with U.S. Federal Government FICAM and FIPS 201 access control standards for agencies and contractors.
- PKI authentication for both physical and logical access, requiring two or more independent combined credentials.
- Enhanced end-user experiences through seamless integration and ongoing support.
HID Global’s strong authentication solutions serve a vital function in managing trusted access to sensitive data and networks, as well as critical and high value assets.

Authentication for Government
- Establishes and proofs identities
- Manages the lifecycle of identities
- Provides physical access
- Authenticates access for IT systems
- Digitally signs email and documents
- Decrypts email and files
- Delivers full disk encryption & boot protection
- Protects print jobs with secure printing
Multi-factor PKI
- Requires two+ combined credentials
- Controls building and secure area access
- Provides onsite and remote login
- Delivers secure access, even in the cloud
- Allows for digital signatures & encryption
- Achieves FICAM and FIPS 201 compliance
- Meets NIST SP 800-116 compliance
- Delivers TWIC reader requirements

Access Control in the Cloud With HID Origo
- Powers a trusted ecosystem of cloud-connected access control devices, applications and trusted mobile identities in one place
- Ensures top-tier service delivery through a scalable and secure infrastructure backed by the world’s leading cloud vendors
- Opens opportunities for adoption of new, more flexible service subscription models
- Provides powerful insights for data-driven decisions
- Validated by industry-leading certifications, including ISO 27001 and EU GDPR
- Designed with an API-first approach, providing programmatic interfaces for all HID Origo services
- Enables Technology Partners to build integrated access control solutions through the cloud









